Advanced Penetration Testing for Modern Threats
We simulate real-world attacks on your systems, apps, and networks so you can discover vulnerabilities before someone else does. Our penetration testing services help you meet compliance, protect sensitive data, and stay one step ahead of modern threats.
What is Penetration Testing?
Penetration Testing That Goes Beyond the Checklist
Penetration testing (or "pen testing") is a controlled simulation of a cyberattack on your infrastructure. Unlike automated scans, penetration tests are performed manually by security experts who think like real hackers. They look for security gaps that could lead to data breaches, ransomware, privilege escalation, or unauthorized access.
At Scalability, we conduct full-scope penetration tests aligned with industry standards like OWASP, PTES, and NIST. Our reports go beyond lists of vulnerabilities, we show how each issue could be exploited and what you need to fix now.
Let’s Talk About How We Can Strengthen Your Security With Real-World Penetration Testing
Why Penetration Testing Matters
Today’s businesses operate in a threat-rich environment. Cloud applications, APIs, mobile apps, remote teams, every surface is a potential target. A penetration test gives you the clarity to address critical risks before they’re exploited.
Pen testing isn’t just for compliance. It’s a proactive investment in your security posture. Whether you're preparing for an audit or launching a new platform, our team helps you uncover and close the gaps - fast.


Who Our Penetration Testing Services Are For
Our penetration testing services are ideal for:
Let’s Talk About How We Can Strengthen Your Security With Real-World Penetration Testing
We don’t just “check the box.” We conduct manual, standards-based penetration tests across your environment - looking for real risks that automated tools miss. Every engagement is tailored to your architecture, goals, and threat model.
Why Choose Scalability for Penetration Testing?
We understand how to work with product teams, security leads, and non-technical stakeholders alike. You won’t get a recycled checklist or an offshore team following a template. You’ll work directly with experienced professionals who take pride in simulating real-world attacks and helping you build defenses that actually hold up.
We care just as much about the clarity of our reports as we do about the depth of our testing. Because at the end of the day, it's not just about what we find it's about how fast you can fix it.

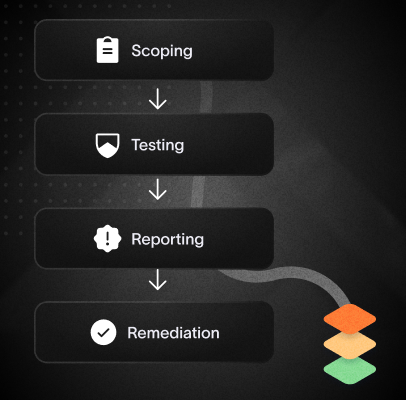
Our Penetration Testing Process
STEP 1
Scoping & Planning
We begin by identifying what should be tested, whether it's your applications, infrastructure, or APIs. This step ensures we focus on areas that align with your security goals, risk profile, and compliance requirements.
STEP 2
Testing and Exploitation
Our team simulates real-world attacks using a combination of manual techniques and specialized tools. We search for vulnerabilities, attempt to exploit them safely, and assess what level of access a real attacker could achieve.
STEP 3
Reporting and Recommendations
After testing is complete, we provide a detailed report outlining our findings. You'll receive technical explanations, risk impact, and clear remediation steps, along with an executive summary for leadership teams.
STEP 4
Remediation and Retesting
We support your team through the remediation process and offer optional retesting to confirm that vulnerabilities have been successfully resolved. This helps ensure your environment is secure and fully up to date.
technology used
We utilize the latest technologies to build high-performing, secure, and scalable websites tailored to your needs. From advanced integrations and AI-powered automation to seamless CRM connections and optimized hosting, our tech stack ensures a seamless digital experience that enhances user engagement and drives results.












How It Works
We begin by understanding your environment, what systems we’re testing, what’s in scope, and where your greatest concerns lie. Then we move through a structured testing process based on leading frameworks like OWASP and PTES.
Every test is performed manually by experienced professionals who specialize in modern attack techniques. We use proven tools, but never rely on them blindly. What matters is what’s exploitable, not just what shows up on a scanner.
At the end, you’ll receive a full report outlining all findings, proof of concept examples, and clear remediation recommendations. We’re also happy to walk your team through each issue, answer technical questions, and retest once changes are made.

Our Service
We tailor every engagement to your goals, infrastructure, and risk tolerance. Whether you're testing a single application or your entire environment, our team delivers depth, clarity, and real-world relevance.
Web Application Penetration Testing
We examine your web applications for critical security flaws, including cross-site scripting, SQL injection, broken authentication, and insecure APIs. Testing is performed manually to uncover business logic issues that automated tools often miss.
Internal & External Network Testing
We simulate attacks from both internal users and outside adversaries to identify vulnerable services, misconfigurations, and paths to escalation. This helps you understand how far a breach could go if perimeter defenses fail.
Mobile App Testing
Our team evaluates your iOS and Android apps for vulnerabilities specific to mobile environments. We test how apps handle data, interact with APIs, and store sensitive information on the device.
Cloud Infrastructure Assessment
We assess your cloud environments in AWS, Azure, or GCP for misconfigurations, exposed services, and privilege risks. The goal is to help your team understand where your cloud setup may fall short of best practices.
API Security Testing
We validate how your APIs handle authentication, authorization, and data exposure. This includes testing for IDOR, insecure tokens, and improper rate limiting that could lead to serious exploitation.
Social Engineering & Phishing Campaigns
We design and execute custom phishing scenarios to test your team’s awareness and response. This reveals how susceptible users may be to manipulation, helping you build stronger internal protocols.
Red Team Engagements
We emulate advanced persistent threats using multi-step attack chains across digital and human vectors. This type of testing is ideal for mature organizations looking to validate their full detection and response capabilities.
Let us handle the technical details and web execution while you focus on growing your business and serving your customers.
FAQs
How is penetration testing different from vulnerability scanning?
Vulnerability scanning is automated and identifies known issues based on signatures. Penetration testing involves human-led exploration that confirms what can actually be exploited, how, and with what impact. It shows the real-world consequences of those vulnerabilities.
What do I need to prepare before a test?
We’ll guide you through the prep. Usually, we’ll need to define the scope of systems or applications to be tested, confirm points of contact, and review any constraints. We’ll also work with you to ensure there’s no disruption to your operations.
Will penetration testing affect our live systems?
No, our tests are designed to be non-destructive. All exploitation is done in a controlled way, and we coordinate closely with your team to avoid downtime. If you're testing a production system, we follow strict rules of engagement.
Can you help us meet compliance requirements?
Yes. We can align your penetration testing with SOC 2, PCI-DSS, HIPAA, ISO 27001, or other frameworks. Our reports are designed to support audit documentation and demonstrate your commitment to security.
How often should we do penetration testing?
At minimum, once a year or any time you launch a major new feature, migrate infrastructure, or make changes to your codebase. Organizations in regulated industries or with fast release cycles often test quarterly.
Do you offer remediation support after the test?
Yes. We provide detailed recommendations for each finding and are available to help your team understand, triage, and resolve them. We also offer retesting to confirm fixes are properly implemented.
Services












